BGP
 Since a core problem with BGP resiliency is the concept of trust, then trust and risk must be a core of the solution. Understanding routing updates as a function of trust and risk enables approaching such updates as partially trusted. Cryptographic solutions attempt to provide perfectly trustworthy sources and paths. Yet Certificate Authority subversion in the TLS realm have shown that today’s certificates are not themselves trustworthy; nor does this proposed solution address misconfiguration or malicious configurations. We propose analysis of BGP from a different perspective, one that recognizes routing as a geographical, economic, political and technical challenges. The result is recognizing routes and updates as partially trusted.
Since a core problem with BGP resiliency is the concept of trust, then trust and risk must be a core of the solution. Understanding routing updates as a function of trust and risk enables approaching such updates as partially trusted. Cryptographic solutions attempt to provide perfectly trustworthy sources and paths. Yet Certificate Authority subversion in the TLS realm have shown that today’s certificates are not themselves trustworthy; nor does this proposed solution address misconfiguration or malicious configurations. We propose analysis of BGP from a different perspective, one that recognizes routing as a geographical, economic, political and technical challenges. The result is recognizing routes and updates as partially trusted.
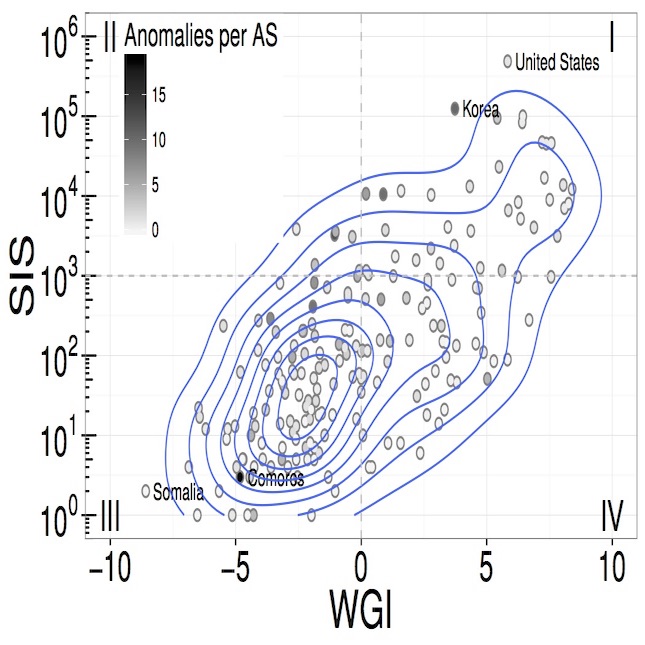
Route updates will be evaluated using both networking and external information. For example, overall change in the RIB would indicate an error, for example route leaks rarely effect only one route. The rate of change in a route is mother indicator: previously consistent routes should not suddenly fluctuate. We also will examine data external to the network. By providing rough geographical estimates (when possible), adjacency, network scale, and market size some hijacking and errors will be detected. For example, a small ISP which has never been a transit route, coming from an identifiable jurisdiction with a history of limited competence that suddenly announces itself as a transit point would be suspect. We combine common metrics, like path length, with market and geographical classifications as a basis for decision-making. The goal is to classify route updates along a continuum of trust, allowing organizations to make their own decisions. Possible decisions include delaying adoption of update, refuse to distribute an update, cease or delay sending information to that route, or simply alerting an operator that some human evaluation or interaction is needed.
We propose analysis of BGP from a different perspective, one that recognizes routes as partially trusted. Route updates will be evaluated using both networking and external information. For example, overall change in the RIB would indicate an error, for example route leaks rarely effect only one route. The rate of change in a route is another indicator: previously consistent routes should not suddenly fluctuate in a stable environment. We will examine data external to the network. By providing rough geographical estimates (when possible), adjacency, network scale, and market size some hijacking and errors will be detected. For example, a small ISP which has never been a transit route, coming from an identifiable jurisdiction with a history of limited competence that suddenly announces itself as a transit point would be suspect. This combines path length with market and geographical classifications as a basis for decision-making.
Publications
| Articles in journals or book chapters (2) |
-
Clint McElroy,
Pablo Moriano,
and L. Jean Camp.
Poster: On Predicting BGP Anomalous Incidents: A Bayesian Approach.
February 2018.

Keywords: BGP, E-Crime, Network Engineering, Governance. [bibtex-entry] -
Pablo Moriano,
Soumya Achar,
and L. Jean Camp.
Incompetents, criminals, or spies: Macroeconomic analysis of routing anomalies.
Computers & Security,
70:319--334,
2017.
Note: Elsevier Advanced Technology.
Keywords: Governance, Macroeconomics, BGP, E-Crime. [bibtex-entry]
| Conference publications (2) |
-
P. Moriano,
R. Hill,
and L. J. Camp.
Hijacking Network Traffic: Temporal Analysis of Adverse Changes in the Internet Topology.
In Conference on Complex Systems,
Thessaloniki, Greece,
September 2018.
Keywords: BGP. [bibtex-entry] -
C. McElroy,
P. Moriano,
and L. J. Camp.
Poster: On Predicting BGP Anomalous Incidents: A Bayesian Approach.
In Network and Distributed System Security Symposium (NDSS),
2018.
Keywords: BGP. [bibtex-entry]
