 | | Internet of Things is rapidly growing and its growth rate has been improving in the last decade. With the introduction of more IoT devices, there has been increasing concerns regarding security and privacy issues included with the usage of these devices. One of the main appeals of IoT is the fact that many devices are connected together which can lead to interoperability of these devices. However, interoperability is a double-edged sword as sharing information between devices can result in more exposure.
|
 | | Physical risks are inherently defined by the physical environment. Cyber security risks are similarly defined by the combined physical and electronic environment. However, unlike the increased risk from speed in the rain on the highway at night, the dimensions of both the combined environment and the nature of the underlying risks are not so obvious. Physical risks are often transparent, and inherently aligned with human information processing capacity: contextual, often visual, and at a pace that fits well within a human narrative. In contrast, cyber risks are ill-suited for human risk perception: either they are literally invisible or identified in a decontextualized manner. There is a critical need in computer security to communicate risks and thereby enable informed decisions by average, non-expert computer users.
|
 | | IoT devices are highly susceptible to cyber attacks and compare to software, they are usually an easier target for vulnerability hunting and eventually pwning. A proper defense against this, is to setup a fine grained firewall where it only allows each IoT device, to communicate with some predefined destinations. For instance, a smart bulb would not need to communicate with a smart toaster, or a smart crock-pot should not communicate with a www.i-am-safe.com.
|
 | | The services offered by mobile apps are useful but these apps can also be privacy invasive, meaning that they compile and share more information than is needed for the task the app performs. For example, researchers at University of California Berkeley analyzed 940 apps and found that one third of them requested permissions for resources that were far beyond what was required for the functionality of the app. Such over-permissioning creates risk to both user security and privacy. These risks exist even in apps for the most vulnerable users, such as those that are designed for children. Currently, Android and iOS privacy ecosystems are grounded in permissions which control access to sensitive resources. These systems explicitly ask users for authorization to allow apps to access sensitive information. Therefore, in is important that permission requests effectively communicate privacy risk to the user so that they can make informed decisions.
|
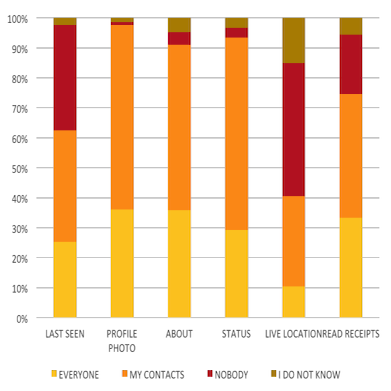 | | Our project involving privacy in social media focuses on studying the usability and implications of the design choices that developers make while building these systems. We look at widely used social networking platforms, especially ones that allow instant messaging, and study user behavior and attitudes on these platforms, and their socio-economic implications.
|
 | | Passwords and Multi-Factor Authentication improve security and protect essential data of users online. However, the usage of simple and guessable passwords or compromised credentials often lead to several threats online, such as, Identity Theft, Financial Loss, etc. Irrespective of attacks, such as spear phishing attacks being present known for a long time, users still fall prey and sometimes fail to adapt to newer and safer technologies. One such technology is multi-factor authentication technology where in addition to passwords and username, users can authenticate through a second or third factor of authentication such as, One Time Passwords, SMSes, Tokens, Biometeric, etc. Our researchers investigate through detailed usability and adaptability research to understand user’s mental models and risk perception and unpack the difficulties an individual face to adapt such secure and helpful technologies. Several reasons contribute to lower security practices by an individual, including the ignorance or lack of knowledge of the users but also poor and transparent risk communication from security practitioners and organizations. Our user studies follow qualitative, quantitative, and mixed methods and provide actionable items and effective insights which contribute in improving the security practices of individuals and in turn enable protecting the online user data.
|
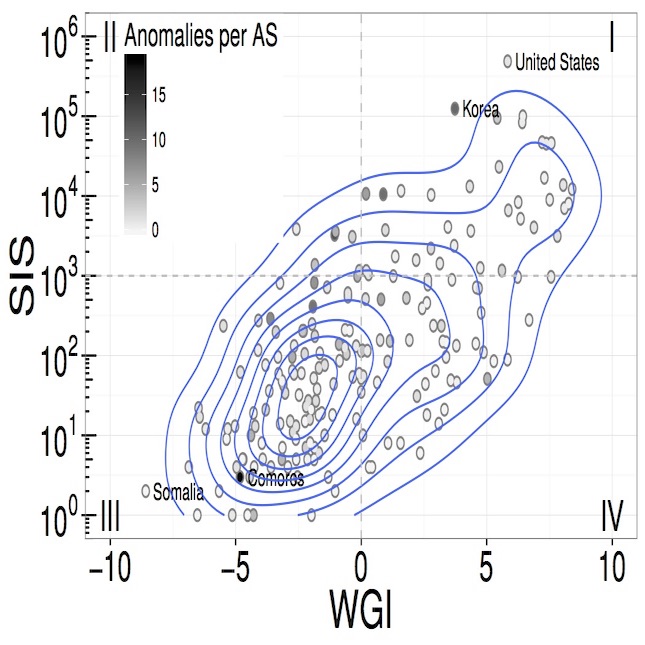 | | Since a core problem with BGP resiliency is the concept of trust, then trust and risk must be a core of the solution. Understanding routing updates as a function of trust and risk enables approaching such updates as partially trusted. Cryptographic solutions attempt to provide perfectly trustworthy sources and paths. Yet Certificate Authority subversion in the TLS realm have shown that today’s certificates are not themselves trustworthy; nor does this proposed solution address misconfiguration or malicious configurations. We propose analysis of BGP from a different perspective, one that recognizes routing as a geographical, economic, political and technical challenges. The result is recognizing routes and updates as partially trusted.
|
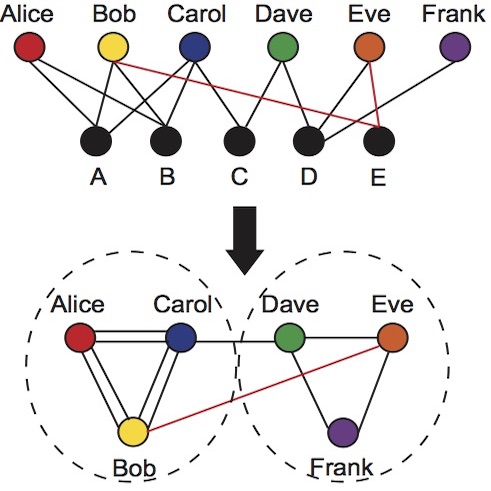 | | The insider threat is fundamentally a problem of human decision-making. Insiders are employees that must be trusted with access to sensitive information, and because of that trust can be a major threat. Insiders attacks are consistently catalogued as the most costly given the elevated privilege that insiders have in terms of trust and access. This makes the insider issue one of the most challenging problems in computer security.
|
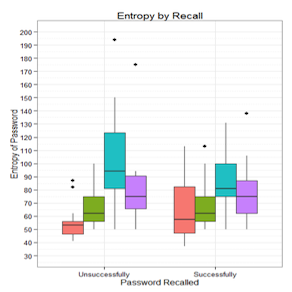 | | Passwords are the primary, most widely used single sign-on and multiple point authentication scheme adapted across the globe. Our research looks at not only how people create and use passwords, but also at external factors that may influence their behavior, such as to what extent changes in password policies and in system requirements impact password usage and reuse.
|
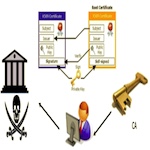 | | Public key certificates are technologies of trust. Many aspects of the current X.509 trust system are broken, illustrated not only by the academic computer security literature, but by recent news stories. Alternative trust models (e.g., Perspectives, DANE, pinning) and modifications to the current infrastructure are built upon threat models that address neither human trust behaviors nor emerging trust domains. Specifically, these alternatives are being proposed in the context of a future network that is integrated with an Internet of Things but are not designed for that environment. Such things and the attributes certified should be aligned with reasonable expectations what the person living with the technology.
|
 | | My work combines large-scale modeling and datasets with targeted smaller experiments to create effective insights for the greater whole. In routing, we combined large scale route views with geographical and political data for measures of trustworthiness of route updates. In certificates we combined small scale local browsing communities with terabytes of certificate data, proving that important features for the detection of rogue and phishing certificates is the geography and governance of the recipient, the entity certified, and the certificate authority. In addition our group has implemented traditional macroeconomic regression techniques to identify features that are correlated with different types of ecrime.
|
 | | Ubiquitous computing (also known as ubicomp)
will be a transformative technology, particularly in the home. Demographic trends, the economics of long term care, new medical technologies, and social norms may collide to result in widespread unexamined adoption of home-based ubicomp and aging. The current model of aging in place cannot be sustained with the retirement and caregiving needs of the Boomer generation. For aging in place, the current model is a single caregiver with complete responsibility for helping the older adult. Aging in Place can lead to social isolation and safety/security risks for increasingly frail elders. New monitoring technologies risk further increasing isolation, as personal caregivers may be less likely to participate in human contact, or offer connectivity based on the design of the system. Without a deeper understanding of privacy, a compelling concern in ubicomp, this transformational change will be framed as a Hobson’s choice: the right to privacy or home-based ubicomp
|
 | | Concerns regarding the environment and the impact humans constantly have on it have been growing concerns for decades, but there is still a substantial lack of environmental literacy and action among most of the population in what they can do to reduce the damage they may be indirectly causing. The environmental impact of technology usage continues to garner attention as fears of built in obsolescence and high turnover of devices contribute to larger negative impacts. Our research aims at increasing environmental literacy and awareness along with giving users actionable steps and interactions to empower them with greater control of their individual carbon outputs and carbon footprints.
|
 | | Accurate communication of risk is not only an issue of high accuracy of underlying data but also in correctly designed simple communication. Past work on risk communication and usable privacy have focused primary on two cases: privacy risk via permissions in Android and security risks in browsing. Accurate feedback requires communication of risk, learning from the feedback, and aligning with user mental models.
|
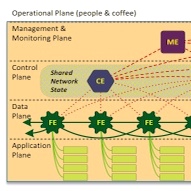 | | What are the challenges, threats, implications and potential for SDN in terms of creating a resilient network? To answer this question, we have created clear threat models grounded in documented and realistic use cases; extracted resulting enumerated authentication requirements; implemented one case of the necessary next-generation network modeling to evaluate authentication interactions, such that the models address all layers from physical to human; and finally the demonstrated practical forward movement to meeting these challenges as an open source network component named Bongo.
|
 | | Models for Enabling Continuous Reconfigurability of Secure Missions, a five-year, $23.2 million cooperative agreement, will form a collaborative research alliance consisting of Indiana University, Penn State, Carnegie Mellon University, University of California Davis, University of California Riverside and the Army Research Laboratory.
|















